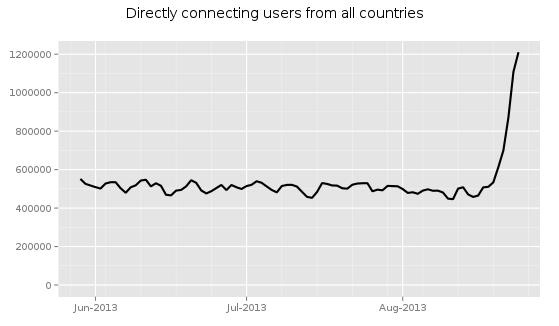
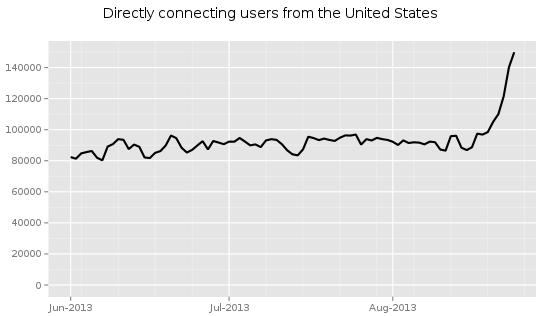
While most of the media, including the alternative media, has been focused primarily on our psychopathic leaders’ attempt to drag us into a Syrian civil war alongside al-Qaeda, some really crucial new information has been released about the NSA from the Snowden documents.
Specifically, we now know the lengths to which the NSA has fought to make encryption useless. Disturbingly, there was a debate about all of this in the 1990’s. Back then the NSA, with the help of the Clinton administration, attempted to install a backdoor into all encryption called a “Clipper Chip.” This was shot down, but the NSA went ahead and did it covertly anyway. This is the type of total unconstitutional slime we are dealing with.
The most absurd part of the recent revelations is the realization that the NSA isn’t actually cracking most of the encryption due to smarts or math, but rather by coercing major technology companies to allow them unfettered access. Part of this coercion unsurprisingly revolves around generous monetary payoffs to “grease the surveillance wheels” courtesy of a hefty Black Budget.
The first highlighted article is from yesterday’s New York Times. The information is so devastating to the already battered reputation of the criminal NSA that according to the paper:
Intelligence officials asked The Times and ProPublica not to publish this article, saying it might prompt foreign targets to switch to new forms of encryption or communications that would be harder to collect or read. The news organizations removed some specific facts but decided to publish the article because of the value of a public debate about government actions that weaken the most powerful privacy tools.
Some key excepts below:
Many users assume — or have been assured by Internet companies — that their data is safe from prying eyes, including those of the government, and the N.S.A. wants to keep it that way. The agency treats its recent successes in deciphering protected information as among its most closely guarded secrets, restricted to those cleared for a highly classified program code-named Bullrun, according to the documents, provided by Edward J. Snowden, the former N.S.A. contractor.
Beginning in 2000, as encryption tools were gradually blanketing the Web, the N.S.A. invested billions of dollars in a clandestine campaign to preserve its ability to eavesdrop. Having lost a public battle in the 1990s to insert its own “back door” in all encryption, it set out to accomplish the same goal by stealth.
The N.S.A. hacked into target computers to snare messages before they were encrypted. In some cases, companies say they were coerced by the government into handing over their master encryption keys or building in a back door. And the agency used its influence as the world’s most experienced code maker to covertly introduce weaknesses into the encryption standards followed by hardware and software developers around the world.
Paul Kocher, a leading cryptographer who helped design the SSL protocol, recalled how the N.S.A. lost the heated national debate in the 1990s about inserting into all encryption a government back door called the Clipper Chip.
“And they went and did it anyway, without telling anyone,” Mr. Kocher said. He said he understood the agency’s mission but was concerned about the danger of allowing it unbridled access to private information.
Intelligence officials asked The Times and ProPublica not to publish this article, saying it might prompt foreign targets to switch to new forms of encryption or communications that would be harder to collect or read. The news organizations removed some specific facts but decided to publish the article because of the value of a public debate about government actions that weaken the most powerful privacy tools.
The full extent of the N.S.A.’s decoding capabilities is known only to a limited group of top analysts from the so-called Five Eyes: the N.S.A. and its counterparts in Britain, Canada, Australia and New Zealand. Only they are cleared for the Bullrun program, the successor to one called Manassas — both names of an American Civil War battle. A parallel GCHQ counterencryption program is called Edgehill, named for the first battle of the English Civil War of the 17th century.
Think about the fact that they named these programs after Civil War battles. What does that tell us about how they view “the people” in relation to government?
Read more
Follow me on Twitter.

 Well, I’m not actually introducing JackPair at all. The creators of the device have had their project on Kickstarter for quite some time now, but it just passed its funding goal today (it had a $35,000 goal and has already raised close to $45,000 as of publication). Congrats guys!
Well, I’m not actually introducing JackPair at all. The creators of the device have had their project on Kickstarter for quite some time now, but it just passed its funding goal today (it had a $35,000 goal and has already raised close to $45,000 as of publication). Congrats guys!